
- Published on
Basics of SSL (Secure Sockets Layer)
- Authors

- Name
- Rahul Neelakantan
What is SSL?
SSL full form is Secure Sockets Layer, a protocol for web browsers for authentication, encryption, and decryption of the data sent over the internet.
Almost every website over the internet uses SSL; if you’ve seen an HTTPS in the address bar or lock icon before it, that means that you’re communicating with the website using SSL. In May 2021, Almost 89% of the websites opened in Chrome are from HTTPS traffic, which has doubled compared since 2015, which was roughly around 40%.
What is Certificate Authority (CA)?
The internet was designed to facilitate quick and efficient open mass communication. Because initially, it was just a communication method. But the internet spread like wildfire, and people started using it for businesses and transferring sensitive data. People with malicious intentions found this open communication system easy to attack and commit fraud.
That is why CA (Certificate Authority) was introduced; they own a unique root certificate. This root certificate is shared with all the major browsers and operating systems. All browsers, operating systems, and devices come with these pre-installed Root Certificates in their root store.
When a CA Certificate Authority approves any digital certificate (SSL certificate), they sign the SSL certificate by their root certificate, a pre-installed trusted root certificate that all the browsers/operating systems have in their store. And that is how CA Certificate Authority companies like DigiCert, GoDaddy, RapidSSL can sell SSL Certificates, which we can include in our server for the secure HTTPS connection.
That is why we can’t sign self sign the SSL certificate because the browsers don’t recognize it. So we must get an SSL from a Certificate Authority.
How does SSL work?
An SSL certificate is a file installed on a website’s origin server. It’s simply a data file containing the public key and the website owner’s identity, along with other information. Without an SSL certificate website’s traffic can’t be encrypted.
Website owners need to obtain an SSL certificate from a certificate authority and then install it on their web server (often, a web host can handle this process). A certificate authority is an outside party who can confirm that the website owner is who they say. They keep a copy of the certificates they issue.
- Secure communication begins with a TLS Handshake, in which the two communicating parties open a secure connection and exchange the public key.
- During the TLS handshake, the two parties generate session keys, and the session keys encrypt and decrypt all communications after the TLS handshake.
- Different session keys are used to encrypt communications in each new session.
- TLS ensures that the party on the server-side, or the website the user is interacting with, is actually who they claim to be
- TLS also ensures that data has not been altered since a message authentication code (MAC) is included with transmissions
Does SSL impact the speed of the Website?
There was a pervasive myth that installing an SSL certificate to the webserver adds too much overhead and slows things down, Yes SSL certificates indeed add some overhead, but it’s less than 1% CPU overhead along with 2% network traffic. But this overhead is nothing compared to the dangers without SSL, where snooping of information is quite possible.
In fact, when Google switched to HTTPS for everything by default, the search giant didn’t deploy additional machines or special hardware. Senior Staff Software Engineer Adam Langley, who works on Google’s HTTPS serving infrastructure and Chrome’s network stack, writes that SSL has a limited impact on web performance.
What is the difference between SSL and TLS?
You may be thinking SSL means Secure Sockets Layer and TLS means Transport Layer Security, so both are different, but actually both are used interchangeably, so there is no difference.
TLS was introduced as the successor to SSL 3.0 in 1999 and was designed to resolve the SSL protocol’s insecurities. So why do all companies provide SSL certificates still? Because they like the name SSL so much, they haven’t named their products TLS. Software that enables SSL on a server, such as OpenSSL, didn’t change their name to OpenTLS. The name SSL was ingrained and just stuck.
Market Share of SSL Providers
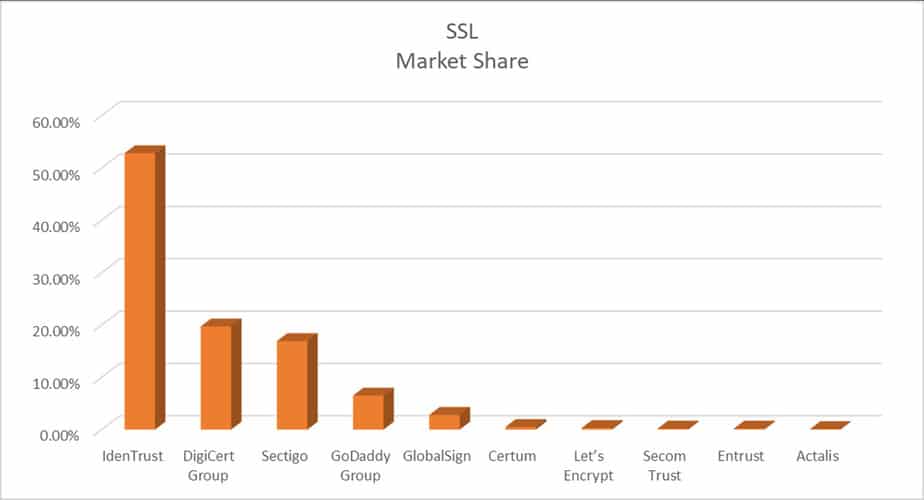
IdenTrust provides SSL certificates for government agencies and banks in the USA. The other major players are DigiCert, Sectigo, and GoDaddy. Let’s Encrypt is one more major player for providing free SSL certificates for Domains. SSL market is Highly competitive, with each player bringing new additions to increase the market share.
SSL Releases
| Protocol | Published | Status |
|---|---|---|
| SSL 1.0 | Unpublished | Unpublished |
| SSL 2.0 | 1995 | Deprecated in 2011 |
| SSL 3.0 | 1996 | Deprecated in 2015 |
| TLS 1.0 | 1999 | Deprecated in 2020 |
| TLS 1.1 | 2006 | Deprecated in 2020 |
| TLS 1.2 | 2008 | |
| TLS 1.3 | 2018 |
SSL 1.0 had several serious security flaws; therefore, it was not released. TLS 1.0 was developed to address some of the common problems with SSL 3.0
TLS 1.3 has numerous advantages to TLS 1.2, these are Faster TLS Handshake, Reduced, stronger cipher suites, and TLS 1.3 only requires 1-RTT (a single round trip) of the protocol, where TLS 1.2 and below required two.
SSL Cipher Suites
If you interact with SSL/TLS and HTTPS encryption long enough, you’re eventually going to come across the term “cipher suite.” And while that sounds like a fancy nickname, cipher suites play a critical role in every HTTPS connection you make on the internet.
Cipher suites are set in your web server configuration. Certificates pretty much work with any cipher suite, independent of how they were issued or who they’re from.
Cipher suites are named combinations of:
- Key Exchange Algorithms (RSA, DH, ECDH, DHE, ECDHE, PSK)
- Authentication/Digital Signature Algorithm (RSA, ECDSA, DSA)
- Bulk Encryption Algorithms (AES, CHACHA20, Camellia, ARIA). AES is the most commonly supported bulk cipher in TLS 1.2 & TLS 1.3 cipher suites.
- Message Authentication Code Algorithms (SHA-256, POLY1305)
TLS 1.3 has eliminated:
- SSL Compression
- Static key exchange functions
- Block ciphers (CBC)
- Non-AEAD ciphers (MAC-then-Encrypt)
- Renegotiation of encryption parameters
It has also dropped support for older, vulnerable SSL ciphers like:
- RC4
- DSA
- MD5
- SHA1
- Weak Elliptic Curves
- RSA Key Exchange
- Static Diffie-Hellman (DH, ECDH)
SSL Validations
There are three basic types of SSL Validations…
- Domain Validation
- Organization Validation
- Extended Validation
Domain validation is simpler to get; basically, the CA Authority needs to validate email and domain WHOIS details.
Organization and Extended Validation are costlier and difficult to get as Organization details, etc., need to be validated by the CA Authority issuing the SSL certificate. Having these certificates is used to show the organization name in the address bar and the padlock for HTTPS connections.
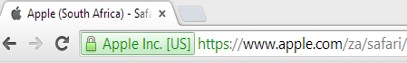
Google and Mozilla have removed the information about extended validation SSL certificates from the address bar after deciding to communicate any useful information to users. For many years, browser vendors have struggled to find effective ways to communicate a given site’s relative security to users. Locks, open or closed or missing, stoplight colors, and various combinations have all been tried.
Google is planning a major change to that in Chrome 77, removing the EV status information from the address bar altogether and moving it into a drop-down instead. The reasoning behind the decision is that people apparently don’t pay much attention to the indicator and don’t miss it when it’s gone.
Conclusion
I hope this post has given you a good basic understanding of how SSL works. For your website to have an HTTPS connection, you’ll need to generate a certificate from a reputed CA like Comodo, Digicert, GoDaddy, etc., as browsers don’t accept self-signed certificates. If you have multiple subdomains, you can look for wildcard SSLs, which can encrypt all subdomains with the same certificate. If you have multiple domains for your business, you can look for Organization or Extended validation certificates.
For a typical small website, the best option would be to go with Let’s Encrypt, or if you have a few dollars to spare, it would be good to take from SSL providers like Comodo, Digicert, etc. If you don’t want to buy a new SSL certificate for each subdomain, the most beneficial option is to go for a wild card SSL.